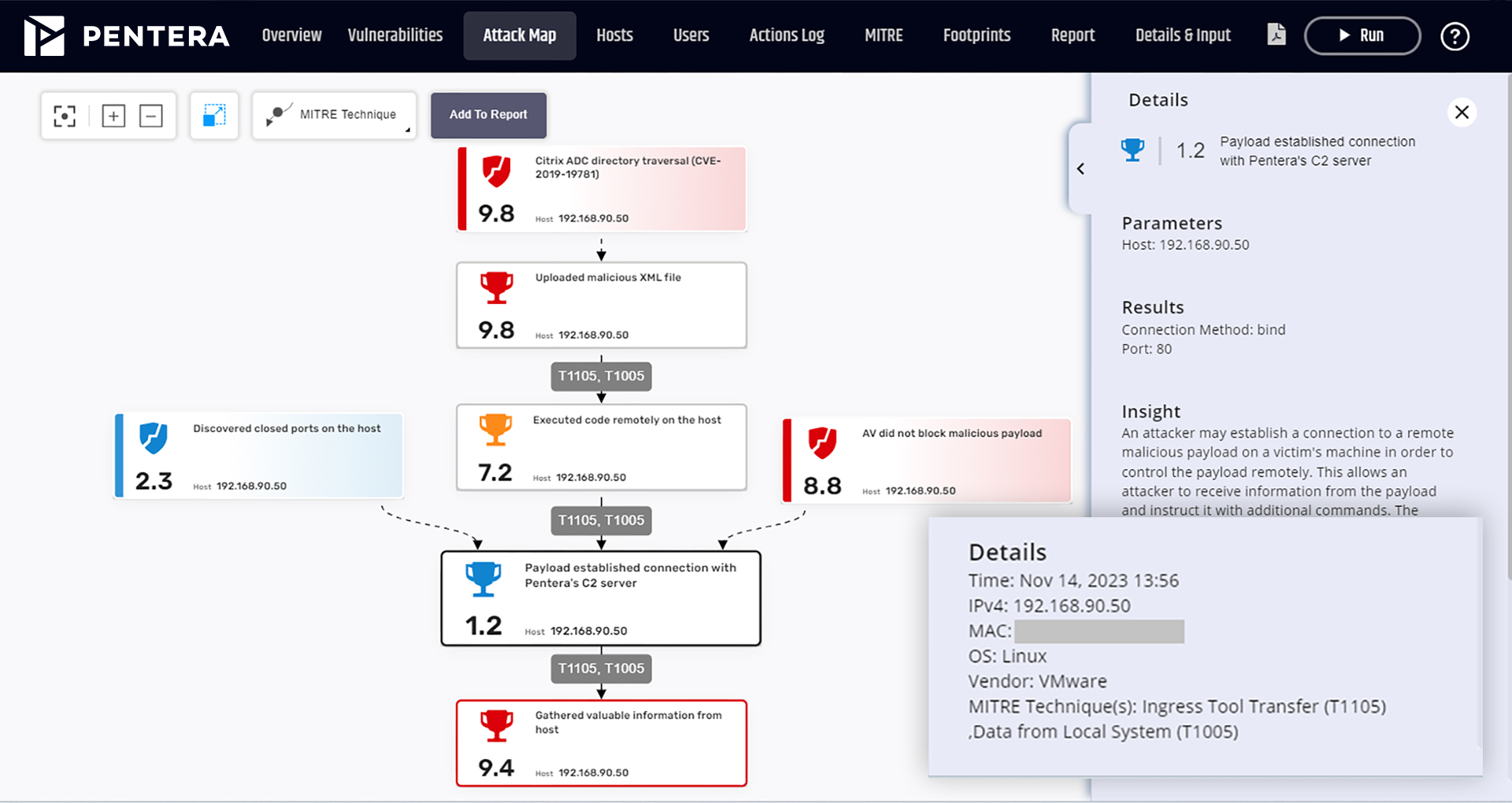
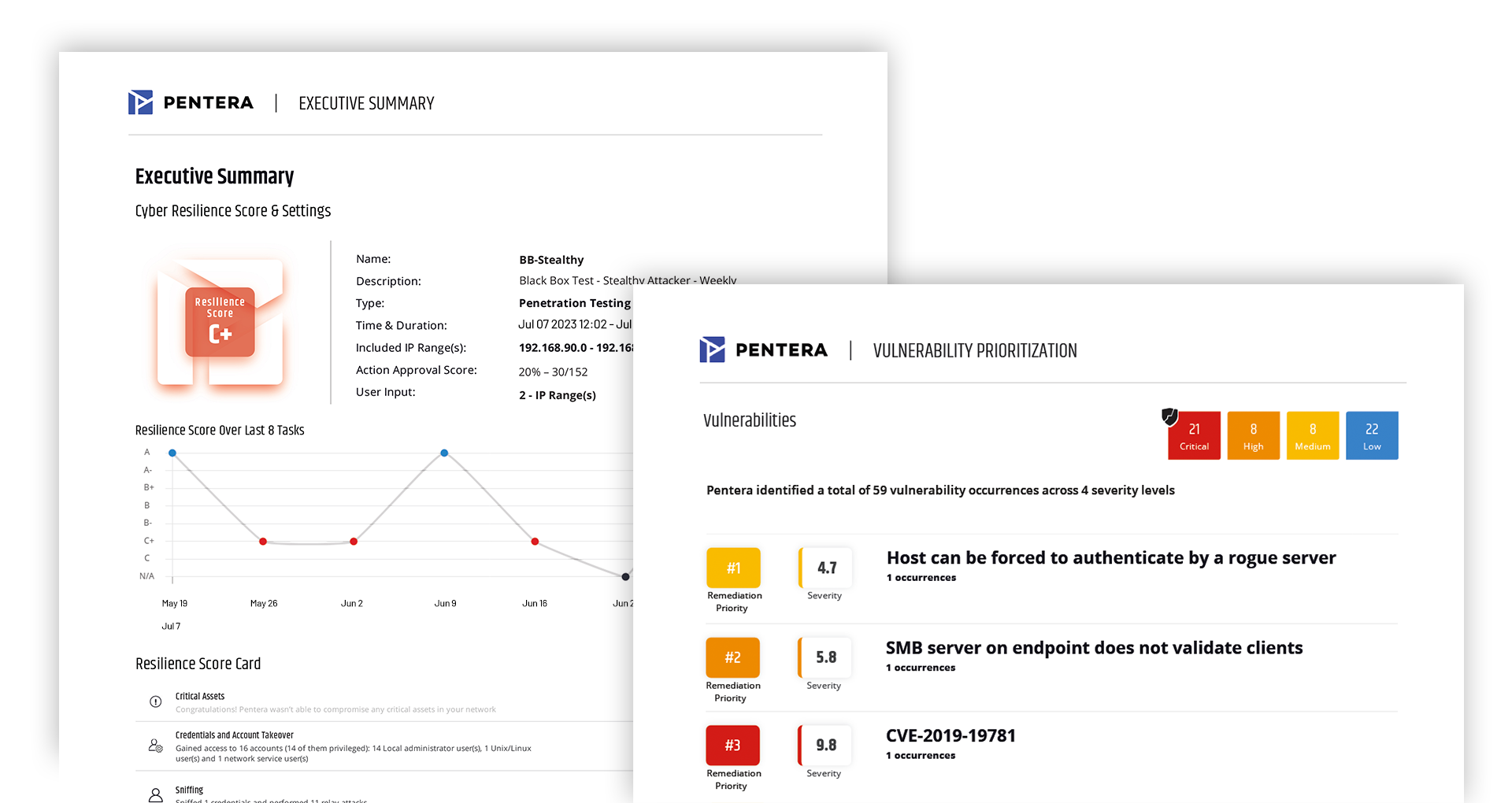
Pentera Platform
Focus your energy on true
security gaps across your
entire attack surface.
Build up your security readiness with Automated Security Validation™.
What your security will look like with us.
Here’s what you can expect.
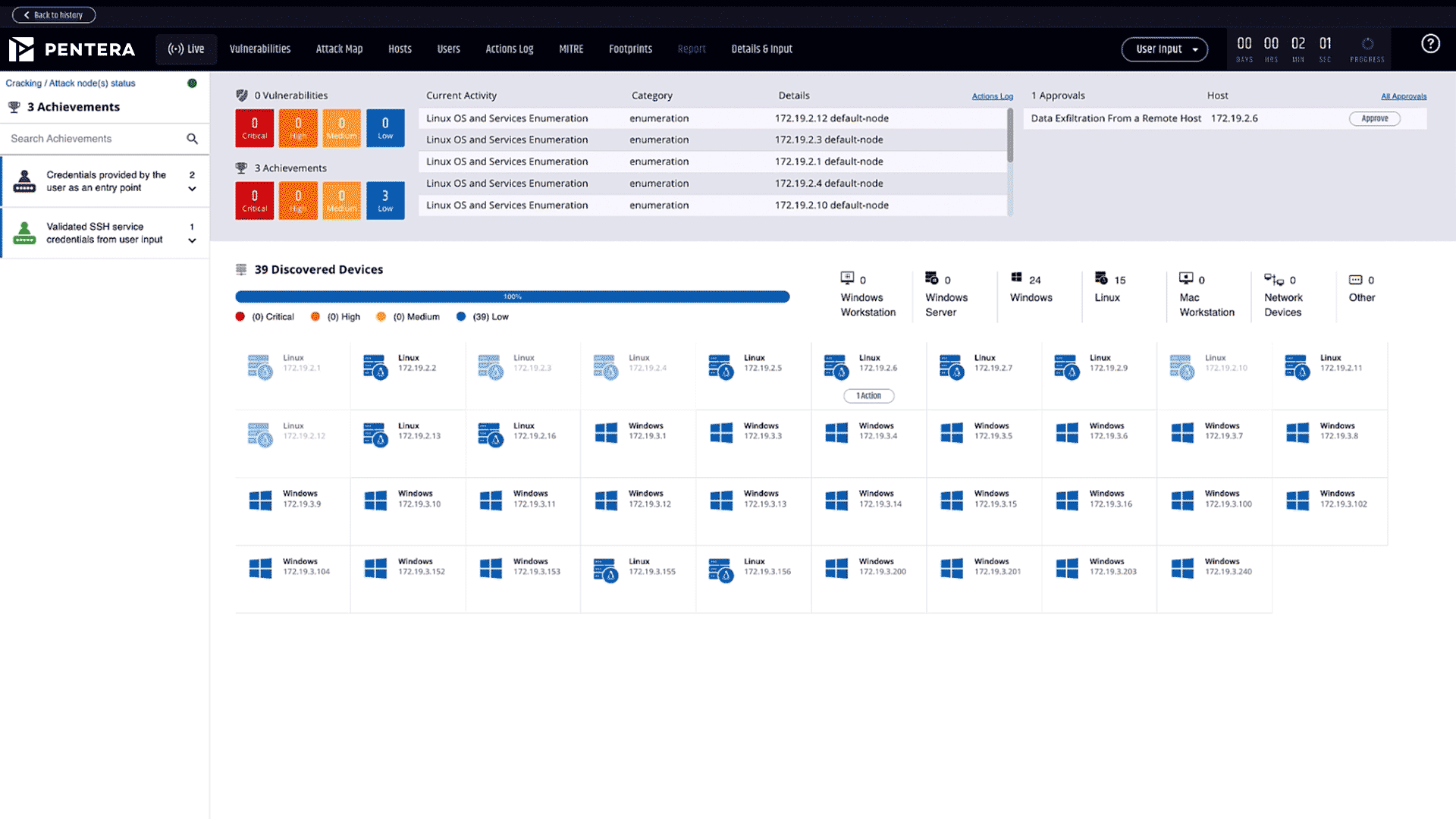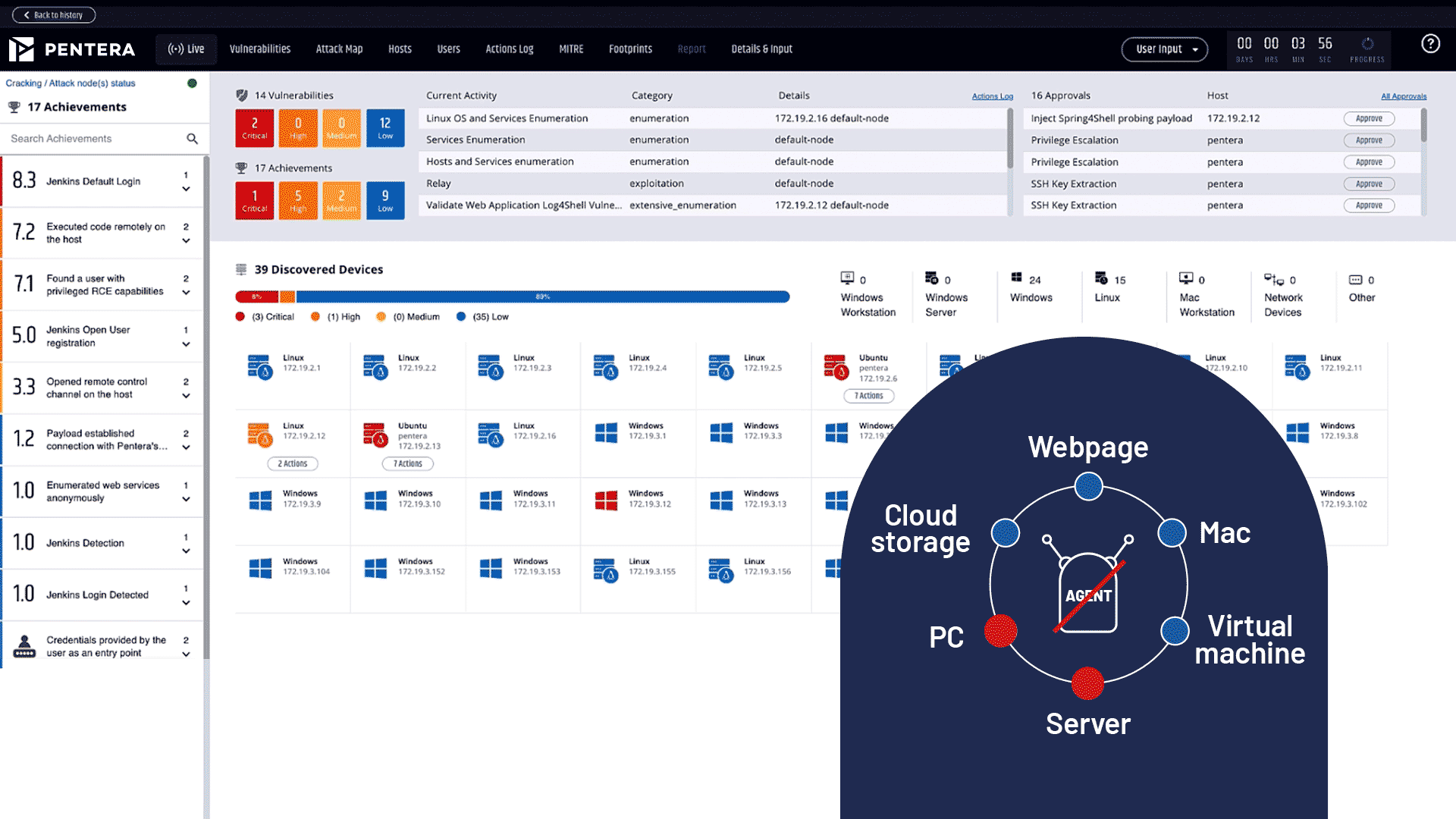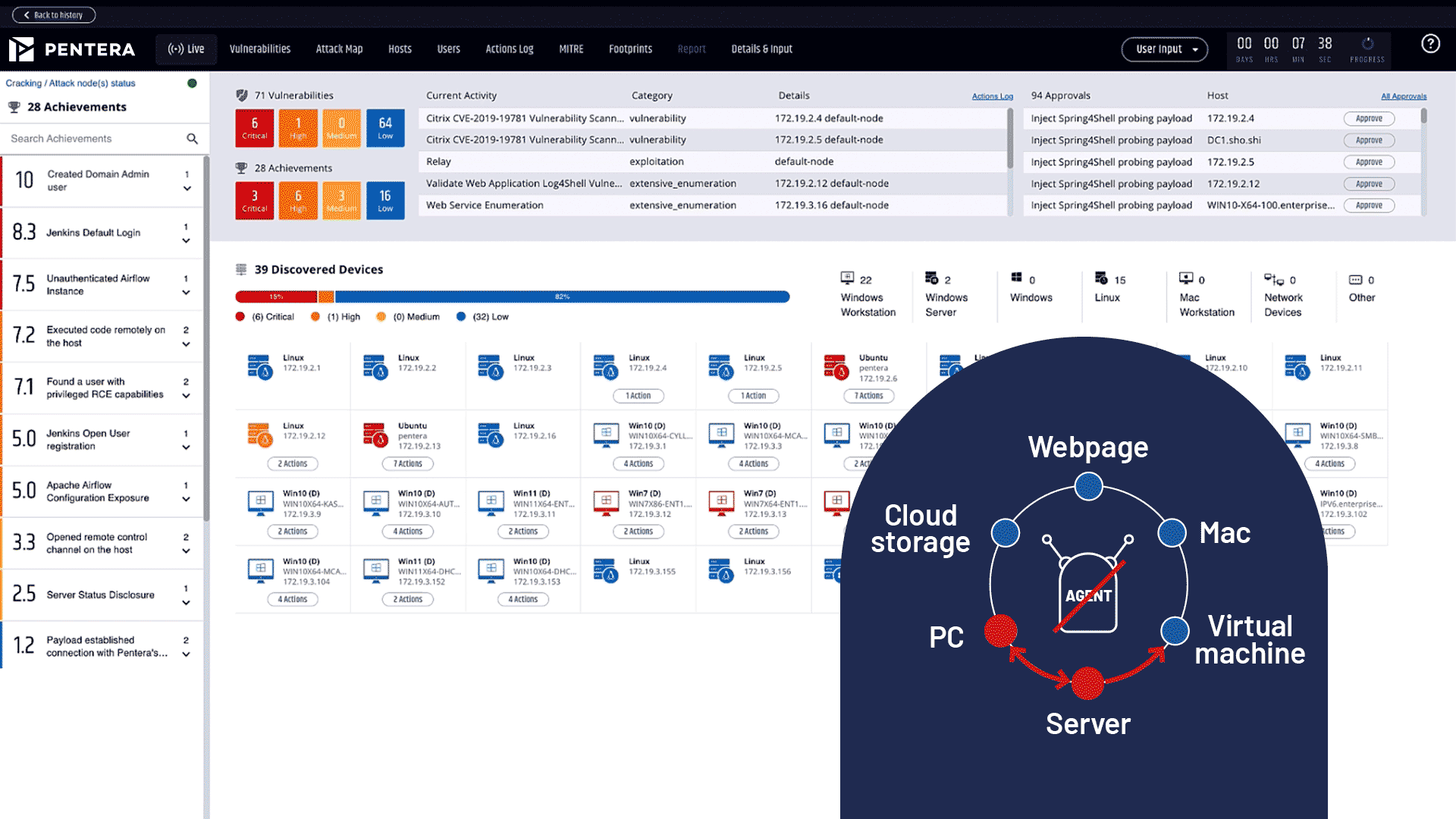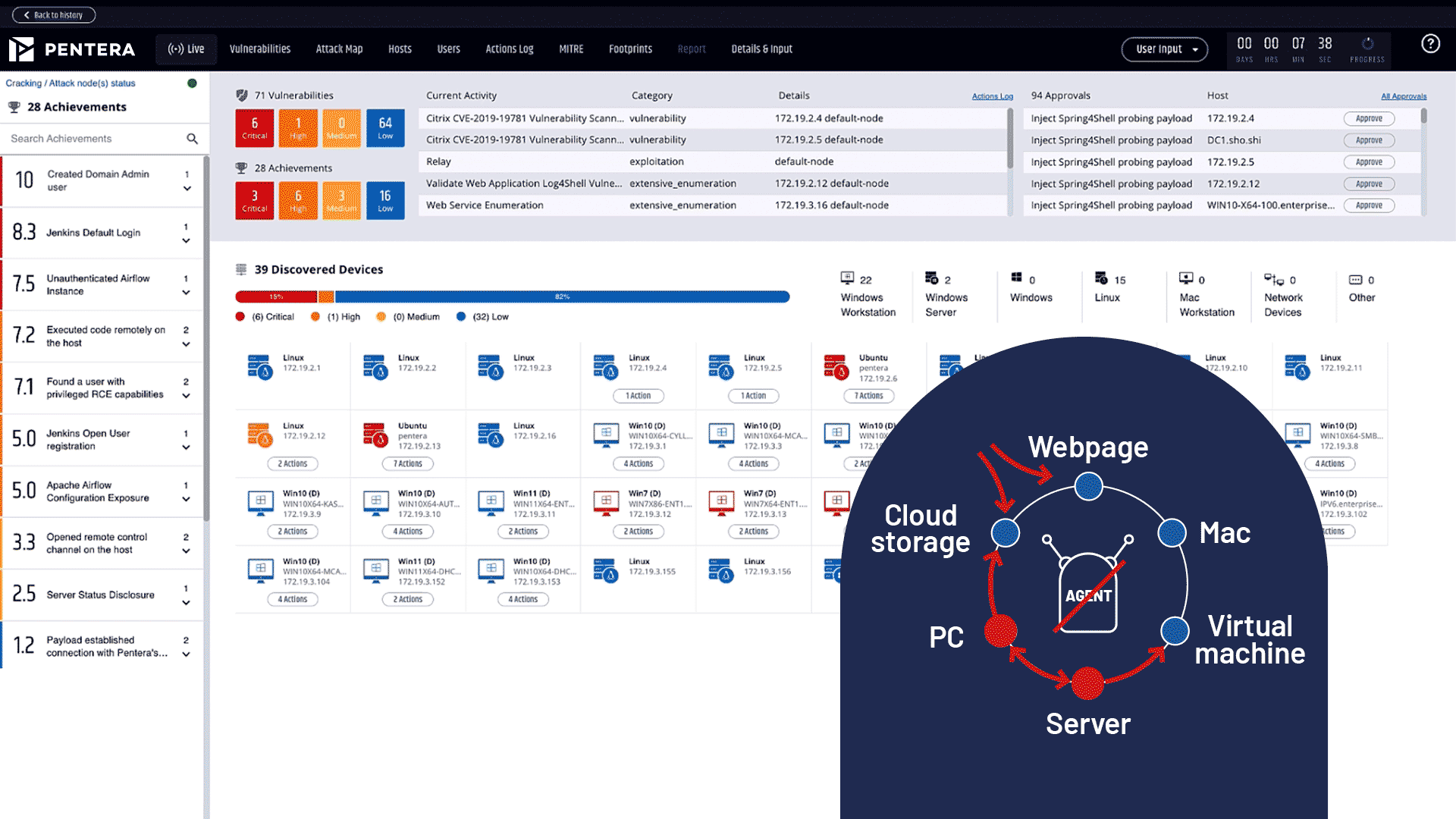
Reduce cyber risk by 80%
Surgically identify critical gaps with algorithm-based automated security validation.
Cut third-party costs by 60%
Continuously test your security controls on-demand without relying on manual audits and outsourced services.
5X team productivity
Provide your team with a clear roadmap to remediation, prioritized based on business impact, so they can focus on fixing what matters.
Discover how our platform
can make a difference for
your security.
Don’t assume. Validate.
All your attack surfaces, tested continuously.